Main methods of hacking facebook account
HII GUys
Now a days every one is searching on net how to hack a Facebook account..Everyone is trying to get the methods of hacking Facebook....I have got some e mails regarding this topic . So I have decided to give a series of post on this topic....Today's post is an introductory post on this topic . I’m now discovering all the methods used to hack Facebook password and some counter measures can also help you protect your Facebook account from hacking.
Following are the main methods used--
1)Facebook Phishing Attack
2)Hacking Facebook password by using Keylogging
3)By hacking the Primary E-mail address
4)Social Engineering or simply guess your password
1)Facebook Phishing Attack:
This is the most easiest and the most popular method for hacking Facebook passwords. I studied the various investigations related to actions about hacking facebook password. The results of these investigations show “phishing” is the main method to hackfacebook password,”Phishing” is a method preferred by facebook hackers. So, friends, phishing facebook Beware. Facebook staff work hard to make these crooks Facebook. Phishing, you can prevent hacking, not only on Facebook, but also virtually every e-mail account. Take Just use the trick to a phisher, which I think is very simple. I have learned without any difficulty. But remember, this is only for educational use.
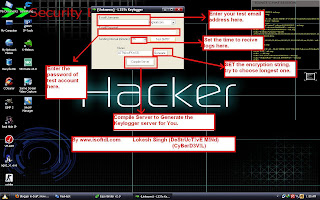
2)Hacking Facebook password by using Keylogging:
This is my second favorite, the only thing you need to do is to install a remote keylogger application (if you do not have physical access to the victim’s computer). Keylogging is easier if you have physical access to the computer victims only have to do is install a keylogger and send it to your aim, so it sends all the recorded keystrokes intended focus. What is a keylogger does is it stores keystrokes in a log file and then can these logs to get the required password and Facebook can not hack facebook password.
3)By hacking the Primary E-mail address:
If a Facebook hacker or any special Keylogger, by any means, hacks your primary Gmail or Yahoo account which you are using as the primary e-mail address, then the hacker can easily hack yourFacebook password by using “forgot password” trich. It is simple for Hackers asks Facebook to send password to the primary email address and ask Facebook administrator to send the reset e-mail to your primary e-mail address which is already hacked. So your Facebook password will be reset and also will be hacked!
So do not forget to try to protect your primary e-mail address and try to keep unknown e-mail or useless e-mail ID as your primary email address.
4)Social Engineering or simply guess your password:
This method seems not enough work at first. Even me, I neglected Sun But when I’m using it against my friend on Facebook and I am his Facebook password very easily with this method. I think many of you know, win what social engineering, for beginners, the social engineering method of recovery password or answer to the question of safety with just the victim. You must be very careful with that victims are not aware of your intention. Ask him carefully with your logic.
Here is some common passwords you can try to guess your password:
1. Your mobile number or your girlfriend or boyfriend mobile number.
2. Your girlfriend or boyfriend names.
3. Date of Birth
4. Your favorite movie names, the names of the cartoon character or favorite band name or names only heroes like Batman, The Dark Knight, Superman, Godzilla, Spartacus, and more ..
5. The main need now, most will forget to ask local alphanumeric now that the user only 1,2,3 smarter in their passwords and some normal guys have added to their passwords !,@,# and surprisingly all right.
So far I have found these Fackbook password hacking methods.